Blog Categories
Popular articles
- Installing, configuring, and using OpenVPN server Centos 6.6
- Module Installation php libssh2 on CentOS 6.x
- Mirror CentALT repository for CentOS 5.x - 6.x
- Attention! Critical vulnerability in all versions of Joomla 1.5, 2.5,3 (CVE-2015-8562)
- S.M.A.R.T - monitor the status of hard drives in Centos sending notifications to Email
Basket of services
Company news
- Thursday, 24 December 2015: Merry Christmas and Happy New Year!
- Monday, 20 April 2015: Accepting payments through payment system Webmoney and Z-Payment restored
- Saturday, 18 April 2015: Unavailable accepting payments via Webmoney and Z-Payment
- Thursday, 05 March 2015: To order new services are available - DNS hosting and secondary DNS server
- Wednesday, 25 February 2015: Added new ways to pay for services
Recent blog posts
-
Attention! Critical vulnerability in all versions of Joomla 1.5, 2.5,3 (CVE-2015-8562)
-
Mirror CentALT repository for CentOS 5.x - 6.x
-
Mozilla after Google announced its intention to abandon the valuable work with sites that do not use https
-
Critical vulnerability in Magento
-
Warning! XSS vulnerability in WordPress and a set plug-ins.
Attention! Critical vulnerability in all versions of Joomla 1.5, 2.5,3 (CVE-2015-8562)
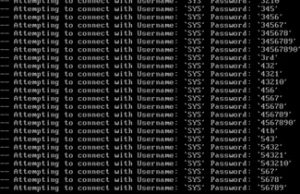
Tuesday, 15 December 2015 10:42A few days ago in all versions of Joomla (1.5, 2.5, 3) found critical (0-day) vulnerability that allows an attacker to successfully attack the sites running Joomla absolutely all versions of the Exploitation of the vulnerability of RCE ("remote code execution") and, as a result, to gain complete control over the site. The attack is made possible due to insufficient filtering of variables in the HTTP request (the field HTTP_USER_AGENT, HTTP_X_FORWARDED_FOR, REMOTE_ADDR) and their subsequent use in the session object, and query a database.
Critical Vulnerability in Joomla 2.5 - 3.3x (CVE-2014-7228)
Wednesday, 01 April 2015 21:53September 30, 2014 it became known about the vulnerability in the software company Akeeba. The vulnerability allows remote upload shell, with no rights in the system. Are affected as the products themselves Akeeba: Akeeba Backup, Akeeba Solo, Akeeba CMS Update, Akeeba Admin Tools, and WARNING: all versions of Joomla 2.5 to version 2.5.27, and 3 to version 3.3.5.
The fact that the standard Joomla component updates using scripts of Akeeba. And Akeeba Joomla and released their updates, covering this vulnerability, but they did not consider it a critical vulnerability, and so many people do not pay much attention to it.
Indeed, a hacker could exploit this vulnerability only when you make a backup copy of your site, or are upgrading the site. That is, it is only a few seconds of which the hacker must still somehow and learn.
Massive brute force passwords from admin panel site by Joomla and WordPress. Hosters disable admin sites
Thursday, 08 August 2013 01:02Of such an attack, we have already written, but in recent days they have intensified with incredible force. The essence of the attack is that the bots of passwords to the admin panel of the website. It is dangerous not only because the password sooner or later they still can pick up, but the fact that it was created a pretty decent load on the server.
Since the attacks in recent days have purchased just incredible strength, the server hosts many simply can not withstand such loads exorbitant. Hosters naturally try to cope with this scourge, but it is they do not always work, as the number of bots is huge and firewalls can not cope with so many locks. Therefore, some of them, as a temporary solution to block requests for files wp-login.php to wordpress and administrator / index.php for Joomla.
Warning! Critical vulnerability in CMS Joomla! Urgently are renewed
Sunday, 04 August 2013 00:52August 1, 2013 came the critical updates for Joomla second and third versions. Vulnerability affects all previous versions, ie version 2.5.13 and earlier line 2.5.x, and version 3.1.4 and earlier line 3.x.
Most likely vulnerabilities are also prone version 1.6.x and 1.7.x
Vulnerability is the ability to download file an unauthorized user, which will inevitably will lead to the breaking of your site.