Blog Categories
Popular articles
- Installing, configuring, and using OpenVPN server Centos 6.6
- Module Installation php libssh2 on CentOS 6.x
- Mirror CentALT repository for CentOS 5.x - 6.x
- Attention! Critical vulnerability in all versions of Joomla 1.5, 2.5,3 (CVE-2015-8562)
- S.M.A.R.T - monitor the status of hard drives in Centos sending notifications to Email
Basket of services
Company news
- Thursday, 24 December 2015: Merry Christmas and Happy New Year!
- Monday, 20 April 2015: Accepting payments through payment system Webmoney and Z-Payment restored
- Saturday, 18 April 2015: Unavailable accepting payments via Webmoney and Z-Payment
- Thursday, 05 March 2015: To order new services are available - DNS hosting and secondary DNS server
- Wednesday, 25 February 2015: Added new ways to pay for services
Recent blog posts
-
Attention! Critical vulnerability in all versions of Joomla 1.5, 2.5,3 (CVE-2015-8562)
-
Mirror CentALT repository for CentOS 5.x - 6.x
-
Mozilla after Google announced its intention to abandon the valuable work with sites that do not use https
-
Critical vulnerability in Magento
-
Warning! XSS vulnerability in WordPress and a set plug-ins.
Quite often there are situations where conventional logging, which writes the apache webserver is not enough. For example, your site is hacked, and you learn a web server logs in order to nahodzheniya hole in your site. If you know the exact time hacking, it is likely that you will find in the logs or script file that was accessed from the POST request. Yes, this will be a POST request. But the trouble is that you will see in the log file only, and that's exactly what he was told, seen unfortunately will not. And the exact time hacking rarely known, so it is usually to find a hole on the website through which it was hacked, very difficult.
Currently, there is a massive network hacking, built on the popular blogging engine WordPress. And in this case, do not use any vulnerability break by brute force banal.
What is interesting, the attack is made with ordinary users' computers infected with the virus. That is, in fact, such a computer is assigned to find the password to a particular site and then he starts every 1 - 2 seconds to try to log into the admin panel of the website. And almost always uses the standard login admin, and the password is moved by a special dictionary. I would also like to note that the brute-force comes not from one infected machine. That is, for example 50 attempts to make a selection of zombie computers, go on two, three and so on. Hacked sites in a similar way at the moment, and a huge number of attacks will not cease.
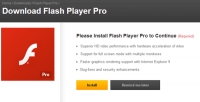
Fake adobe flash player update virus infects computers and phones users
Sunday, 24 March 2013 00:28In recent years, often traveling to different sites on the Internet, you can see the warning that the version of Adobe Flash Player on your computer is outdated and it needs to be urgently updated.
Warning! Be careful. A huge number of these alerts are false (the fake) are not on the website of Adobe, and installing such update to your computer or phone, you own it contracted the virus.
How to distinguish a fake from the moment an alert? It's pretty simple. We will try to detail everything in detail.
So, since you're reading this, it means your site is likely been compromised and now you need to eliminate the consequences of breaking. Who and what could hack your site, you can read in our previous article, "How and why to break sites", and here is how to eliminate the consequences of breaking, we will try to summarize in this article.
Initially, we want you to understand - that if your site is hacked, it means to him that something is wrong and it can crack again and again. That is, before proceeding to eliminate the effects - initially need to determine and correct the cause cracking. Otherwise you hacked tomorrow, or even at a time when you are eliminating the consequences of breaking.
I'm sure many of you surf the Internet there are sites at the entrance which starts to swear antivirus, or even instead of the site hangs completely different page or site redirects you to an unknown destination. And the daily news headlines are full of headlines that unknown hackers broke into one or another popular site. The owners of these sites know this not by hearsay, because daily hack several thousand web sites and get into this wave can be absolutely any resource. Absolutely safe code and the software does not happen, and this axiom to be learned.